It is estimated that every 11 seconds there’s a ransomware attack. And when it comes to cyberattacks aimed at businesses, Canada is second only to the US. Could your business be next?

Predators are lurking in the concrete jungle…
Ransomware is the latest form of cyberattack and the epidemic is quickly spreading across the globe. In fact, there’s been a noticeable 363% increase year over year, of ransomware attacks, targeting business clients and the software they use.
The effects can be devastating to any business, large or small, costing thousands of dollars in ransom (sometimes even millions), the loss of important data, and days of down time. And these hacker attacks are often triggered by a well-intentioned employee who simply opened an email or attachment.
So, how do you protect your business from a costly ransomware attack? We’ll explore a couple of common scenarios and how you can safeguard your devices and IT systems.
The Simplest Things Can Infect Your Systems
Once a ransomware attack is triggered, there’s not much you can do. By then, the perpetrator has already locked you out of your device and/or files and will demand a ransom to restore access.
That’s why the best protection is prevention. Here are some things to be wary of…
How to Avoid Evil Email Attachments
Attachments may appear legit. They may look as if they come from someone you know – oh, look, it’s from Aunt Elly or from a coworker… But wait. Looks are often deceiving.
Hackers often fake (or “spoof”) email addresses to make them seem familiar. Or they use fear as motivation to get you to open the attachment. But follow these three rules and you will be much safer.
Our three rules for opening attachments:
Rule #1: Even if it looks like it comes from a trusted source, NEVER open an attachment that you’re not expecting. Instead, contact the person in a separate email and ask them why they sent it to you or pick up the phone and call them. DO NOT proceed without confirmation!
Rule #2: If an email starts out with a warning about being late with an invoice or threatens you with legal action, or some other unwanted penalty, beware! Hackers often use fear to motivate you into opening their attachment.
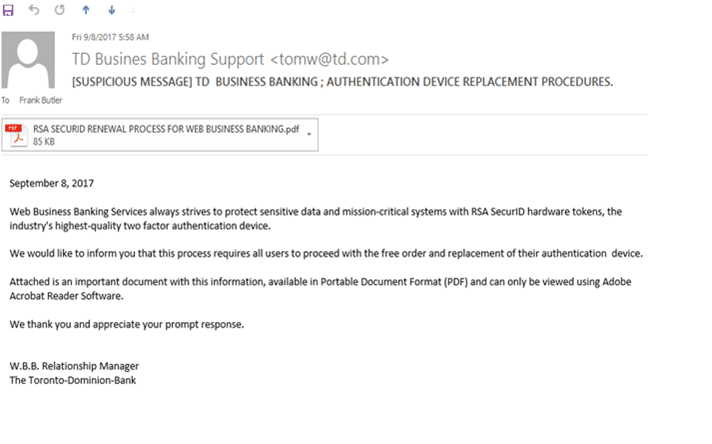
Rule #3: If you receive an email with an attachment that appears to come from a bank or financial institution, throw it away. Even if it looks like this (see Figure 1).
There are also some dead giveaways to look for:
See how the email in Figure 1 doesn’t address anyone specifically? If a bank sends you something, trust us, it will have your name on it.
Also, notice how there’s no personal signature? It doesn’t say who it’s coming from. Banks will always have a signature line from a person, not a department. And remember, just because it says it is from tomw@td.com doesn’t mean it is from tomw@td.com. It may be spoofed.
Now, if you’re expecting something from your banker or financial planner, that’s different. But the key point is banks don’t send out unsolicited attachments.
A Word on PDFs…
What if it’s just a PDF? What could possibly go wrong?
Sometimes PDFs aren’t actually PDFs. Instead, they’re scripted programs that can infect your computer. So you probably shouldn’t take a chance.
But what if it looks like a simple PDF. How do you tell if it’s OK to open?
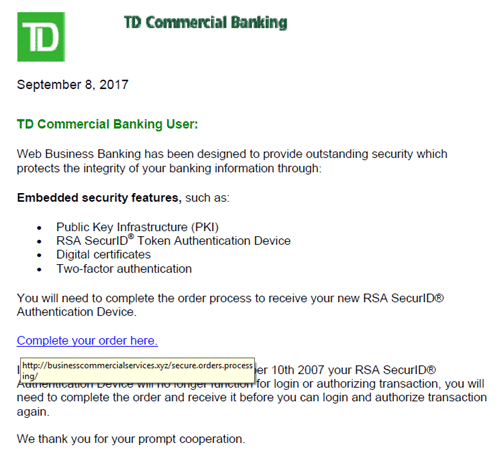
Let’s look a little closer at that so-called “PDF”, particularly the link in Figure 2.
The best way to tell where a link actually goes is to simply hover you mouse over the link for a few seconds.
In our example below, you can see what happens if you were to hover your mouse over the link. As you can see, it does NOT take you to the Toronto Dominion Bank. It goes somewhere else. And this is the best way to tell if your link is legit. In this situation, if it doesn’t go to the bank, it’s bogus.
Also, notice how the hacker mistakenly put the date as 2007, instead of 2017? No one ever said hackers are smart. The wording also tries to scare you by saying that your online banking won’t work unless you follow these instructions. Again, another common tactic of an online fraudster attempting a ransomware attack.
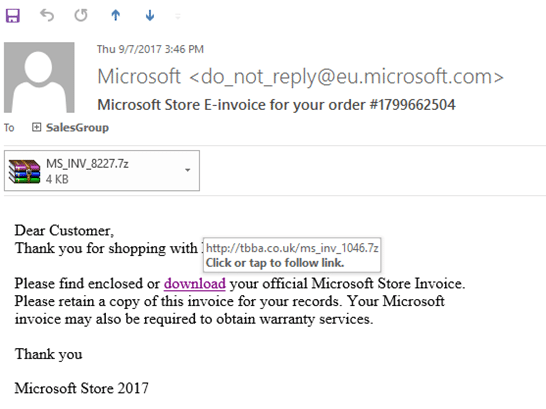
Here’s another example (See Figure 3 below).
In this case, the attachment is supposedly from Microsoft, for a purchase you allegedly made. Of course you don’t remember making one, so this ploy might not work on you. But the hacker figures if they send out enough emails, they will eventually land on someone who has made a recent purchase at the Microsoft Store.
Don’t want to be the next victim?
Some Essential Clues for Spotting False Attachments for Online Purchases
Clue#1: Notice the attachment is a zip file (you can tell by the .7s extension on the file name). This is your first clue. Who sends out an invoice in a zip file? No one.
Clue #2: Your second clue? It is not addressed to you specifically. No one sends an invoice to “Customer”. This email is extremely dangerous – throw it away. If you did buy something from the Microsoft Store, you probably have an invoice already. And if you’ve somehow forgotten to pay, the vendor will eventually contact you or find you, even if you do ignore their emails.
Clue #3: Notice Figure 3 below – when we hover our mouse over the download link, it does NOT go to a Microsoft site. That is your biggest red flag. In fact, 95% of ransomware attacks would be prevented if everyone learned the simple trick of “hovering”. It’s your #1 defense against malicious links.
Be “On Guard” For Bad Web Links
Even more common than emails with bad attachments are emails with bad links. Be suspicious of any emails that contain web links, especially unsolicited emails.
Mostly designed around popular services and/or banking and financial institutions, you will often see this kind of hacker attack for services such as Dropbox, PayPal, Apple, Microsoft and <insert your bank here>.
The hook is usually centered around fear. The attacker will scare you into believing that an account suspension is eminent unless you immediately act.
However, it is very unlikely that Dropbox, Apple, or anyone else for that matter, will suspend your service just because you didn’t click on a link they sent. In reality, they won’t ever send you a link for a “suspension of service”. If in doubt, contact them directly, to verify that your notice of suspension is authentic.
Also, examine the email more closely before hitting reply or clicking a link.
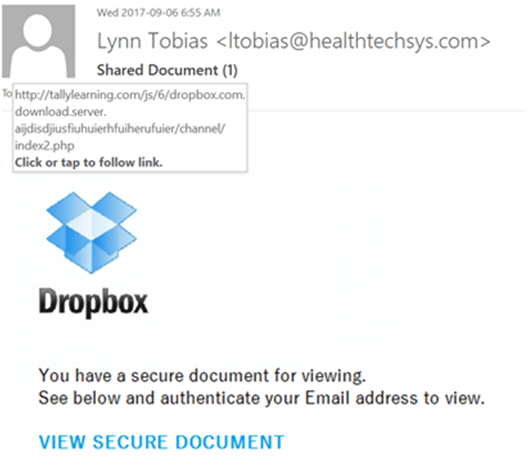
See this example below (Figure 4)? It’s supposedly from Dropbox. But let’s take a closer look.

All we’ve done is hover over the email link with our mouse. See how it leads somewhere else, other than a Dropbox site?
Also, the email instructs you to follow this link to complete your signup to Dropbox.
The question to ask yourself is: did you take that action?
If you haven’t recently signed up, there would be no reason to receive this email. This is red flag #2.
If “hovering” shows a link to somewhere different, that’s when you know it’s not the real deal. Delete this email with extreme prejudice. Or in the words of Arnold Schwarzenegger: “Terminate it.”
Here’s another one…
See Figure 5? It’s similar to Figure 4, in that it’s another Dropbox email. The main difference is that the sender is not a generic email, like no-reply@dropbox.com. It’s someone by the name of Lynn Tobias.
So, how do I know if this is really a trusted person, a scammer or even a ransomware attack?
Ask yourself:
- Do I know anyone named Lynn Tobias? (Probably not).
- Have I ever worked with anyone from healthtechsys.com or tallylearning.com? (Again, probably not).
- Am I expecting any documents from anyone? (In this case, no).
- When I hover over the link, does it go somewhere other than a Dropbox site? (In this case, yes).
Did this email link pass the test? No. In that case, it’s a resounding fail. Do not open it!
Which brings us to the third most common method of ransomware infection…
The Penalty for Poor Passwords
You knew we were going to include passwords in this discussion, didn’t you?
The fact is we all have resources on our network that interface with the outside world: Email servers, remote access servers (terminal server), corporate websites, etc. While these may be strongly protected resources, the reason they become vulnerable is by bad password practice.
What is that? Here’s an example of Bad, Better and Best Practices when it comes to password use (or the Good, the Bad, and the Ugly).
Bad Password Practice (i.e. “The Ugly”):
You know the ones we’re talking about. Passwords such as: password, P@ssword, 12345, qwerty, Missy123, or any combination of your kid’s name or birthday, or family dog, etc.
Why would anyone choose such an easy password to protect their most vital systems?
The reason we create passwords like this is because we want to be able to remember them. Problem is a hacker can crack a simple password in seconds. And if you use the same password everywhere, to avoid multiple logins as soon as they guess one password – voila! The attacker now has access to everything.
Better Password Practice (i.e. “The Bad, but not so bad”)
The better way to do things would be to set up different passwords for every single login you have. Passwords should also be a minimum of 8-12 characters, with one capital, one numeral, and one special character (such as a $ sign or ?).
But even that strategy is less than optimal because a good password cracker can figure out almost any combination in 5 days, even using the above elements. Remember, hackers usually use armies of infected PCs (botnets) to do their bidding. Once the bots are fired up, the hacker just sits back and waits for a successful breach.
Best Password Practice (i.e. “The Good”)
The best practice for creating strong uncrackable passwords? Use a password sentence instead. Something like “My all-time favourite dish is pasta Bolognese”.
That type of password could take hundreds to thousands of years to crack.
Add in a few intentionally misspelled words, some caps, and special characters (even an extra space or two), and you end up with an even stronger password like “My all-time favrit3 deesh is pasta Bologneeze!”
This password could take roughly 200 million years to crack! Seriously, 200 million years. Hard to remember? Yes. But impossible to crack.
Parting Words on Password Protection
If you worry about keeping track of all these different, unique passwords, then get a password vault – there are tons of good ones out there and most are free.
Also make sure you protect your password vault with another strong, hard-to-guess password or better yet, biometrics (fingerprint reader). It’s more difficult to steal someone’s fingerprint than a password – unless the perpetrator is James Bond.
Finally, the other thing you want to keep in mind is all your various social media accounts. If you have a habit of constructing passwords that are made up of family member names, birthdays, pets, or vacation spots, you may want to restrict the amount of information you share on Facebook or anywhere else.
Anyone looking to target a company will most likely target the employees first.
Passwords built on easily mined information are truly a weak spot and one that hackers will exploit.
Key Take Away from Our Ransomware Rundown:
- Never open unsolicited emails, attachments, or web links. Even if it looks like it comes from a trusted source.
- Before opening any attachments, verify by sending your own email to the sender (do not reply to the original email which could be a scam). Better yet, phone the sender to ensure it’s legit.
- Don’t give into fear. Hackers will often try to scare you into opening a link or attachment, by threatening you with account suspension or legal action.
- Scrutinize your emails carefully, especially if they contain a link. If it comes from a generic email, doesn’t contain your name, isn’t solicited by you, and/or doesn’t pass the mouse hover test, delete them.
- Beware of emails, attachments or links that appear to come from financial institutions. A legit bank or business will NOT generally send you unsolicited emails about important financial matters, unless you specifically request one from your financial planner or banker.
- Follow password “best practices” and create strong uncrackable passwords for each login. Or consider using a password sentence instead, especially a misspelled one with unique characters.
Really, all these techniques are commonsense approaches. Follow these simple steps and you will reduce your risk of a ransomware infection by over 90%. Fail to do so and you may end up on the wrong end of a ransomware demand, something that could cost your business thousands of dollars to fix.
Need the reassurance of Managed IT, system backups and disaster recovery plans? Check out our Managed IT services.


