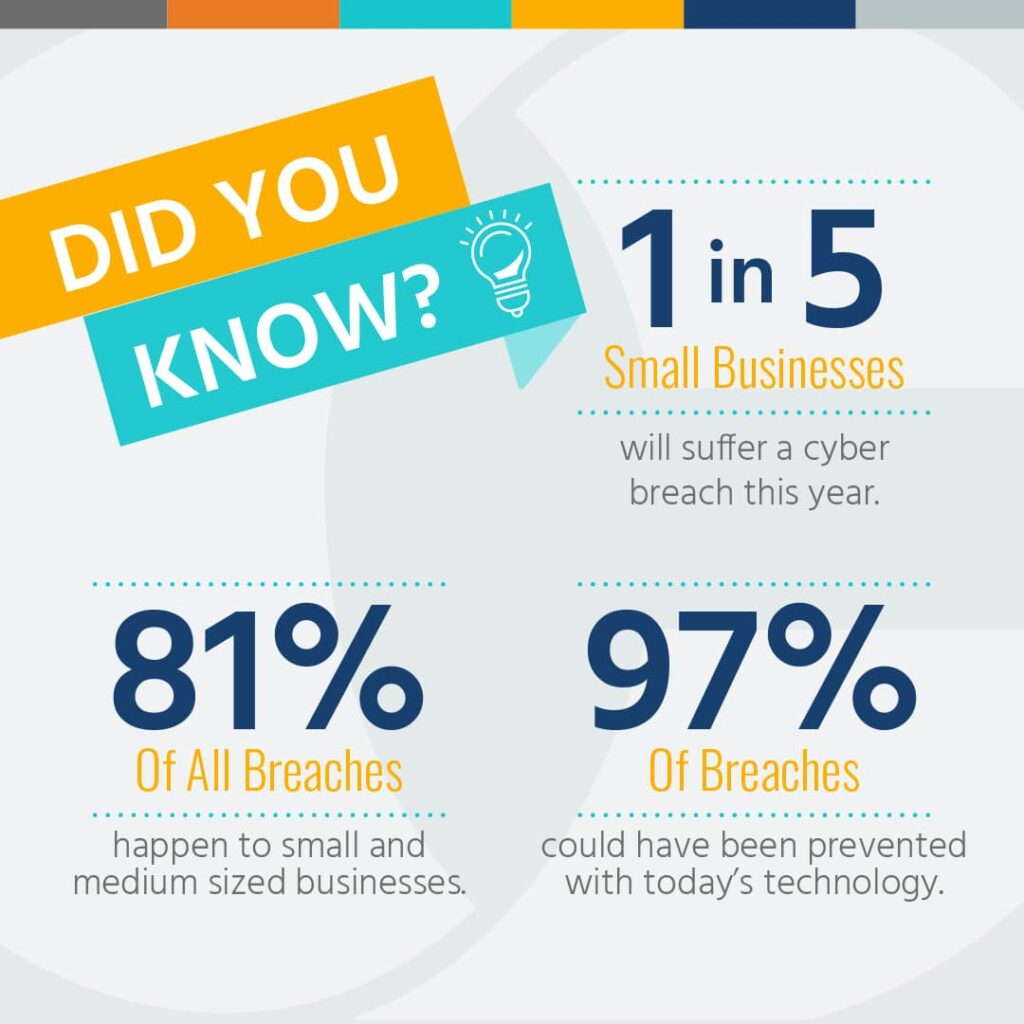
Your business is your castle, and it’s under threat of attack. But don’t worry, we’ll show you how to build strong defences and be prepared to battle hackers with effective cybersecurity tools and procedures. Here are 15 ways to protect your business from a cyberattack.
15 Ways to Protect Your Business from a Cyberattack
Perform a Security Assessment
It’s important to establish a baseline and close existing vulnerabilities. When was your last assessment? Take an in-depth look at your current cyber security tools, and make a note of where they can be improved.
Block Those Spam Emails
Take steps to secure your email. Did you know that most cyberattacks originate in your email? We can help you choose a service designed to reduce spam and your exposure to attacks on your staff via email.
Use Passwords to Guard Access
Apply security policies on your network for an added layer of protection. Great examples of these are to: deny or limit USB file storage access, enable enhanced password policies, set user screen timeouts, and limit user access.
Heighten Security Awareness
Train your users to recognize threats and utilize cybersecurity tools. Teach them about data security, email attacks, and your company’s policies and procedures. To put this knowledge to the test, use a web-based training solution to keep everyone practiced and up-to-date.
Employ Advanced Endpoint Detection & Response
Be sure to protect your computer’s data from malware, viruses, and cyberattacks with advanced endpoint security. Today’s latest technology replaces your outdated antivirus solutions, and protects against file-less and script-based threats. It can even rollback a ransomware attack.
Enable Multi-Factor Authentication
Utilize Multi-Factor Authentication whenever you can, including on your network, banking websites, and even social media. Adding security questions or text messages as an additional authentication step adds an additional layer of protection, ensuring that even if your password does get stolen, your data stays protected.
Does your cybersecurity plan check out? Download our checklist to ensure you’ve covered every angle.
Run those Computer Updates
Don’t ignore update notifications, they may include important security fixes. Keep Microsoft, Adobe, and Java products updated to keep your security tight. We can provide a “critical update” service via automation to protect your computers from the latest known attacks.
Do Some Dark Web Research
Have your passwords been compromised? Knowing in real-time what passwords and accounts have been posted on the Dark Web will allow you to be proactive in preventing a data breach. We scan the Dark Web and take action to protect your business from stolen credentials that have been posted for sale.
Security Incident & Event Management (SIEM) and Log Management
SIEM and Log Management are two software tools that use big data engines to review all event and security logs from all covered devices. This protects against advanced threats and meets compliance requirements.
Web Gateway Security
Internet security is often a race against time. Don’t just react. Stop the threat before you even know it’s there. Cloud-based security detects web and email threats as they emerge on the internet, and blocks them on your network within seconds, preventing them from reaching you.
Mobile Device Security
Today’s cybercriminals often attempt to steal data or access your network by way of your employee’s phones and tablets, which can be less secure than your organization’s network. They’re counting on you to neglect this piece of the puzzle and leave the devices vulnerable. Mobile device security closes this gap.
Engage your Firewall
Turn on Intrusion Detection and Intrusion Prevention features and send the log files to a managed SIEM. If you’re not sure what these things are, get in touch to learn more.
Use Encryption
Whenever possible, the goal is to encrypt files at rest, in motion (think email) and especially on mobile devices. Encryption protects data by encoding it so it remains hidden or inaccessible to unauthorized users.
Don’t Forget to Backup
We can’t stress the importance of a backup enough! Backup local, backup to the cloud, and have an offline backup for each month of the year. To ensure your backups are working properly, test your backups regularly.
Cyber Insurance: If all else fails, protect your income and business with cyber damage and recovery insurance policies.
How many of these procedures or tools do you already have in place? Where are your defences weak? At Com Pro, we’ll ensure your IT infrastructure is secure against any external threats with a tailor-made protection plan. Review all 15 ways to protect your business from a cyberattack, and then give us a call to learn more.